CONFIDENCE. CONTROL. CAPABILITY.
Data Operationalization & Agility Through Security


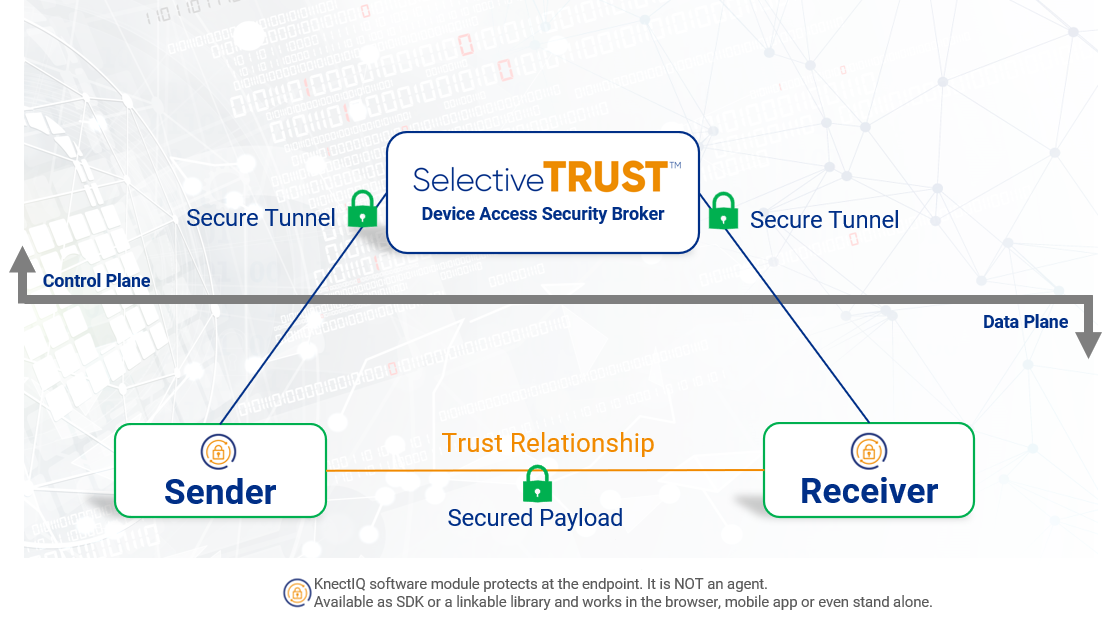
SelectiveTRUST™ technology is a groundbreaking solution to the challenges of multi-domain interoperability. It establishes secure trust relationships at the device level with fine-grain controls to preserve national or enterprise digital sovereignty while at the same time enabling on-demand trusted collaboration across multiple domains.
By implementing SelectiveTRUST, military forces, government agencies, and nation states can ensure that communications and data exchanges are secure and controlled, in real-time, on-demand, with added collaborative capability that enhances current data operationalization methods.
SelectiveTRUST security infrastructure provides unprecedented data-centric agility for interoperability advantages. It uniquely enhances and extends Zero Trust frameworks to remove barriers for safe data operations that maximize operational capacity with real-time security and agility to ensure mission success.
SelectiveTRUST securely authenticates and authorizes access for every trusted device, every transaction/communication, in any environment, at all classification levels, in real-time, without requiring new infrastructure.
SelectiveTRUST™ by KnectIQ:
- Enhances Zero Trust transformation with operational data agility
- Secures reliable connectivity to all trusted devices, everywhere, in real time, in any existing environment, at any classification level
- Provides quantum-capable data protection through agile, adaptive, modern, and ephemeral cryptographic operations
- Delivers real-time cryptographic flexibility, data agility, interoperability, and high availability for full spectrum C5ISR&T
- Enables secure communications and provides solutions within the JADC2 framework
Ultra-Secure Solution

Technology Highlights
How does SelectiveTRUST™ work?
INTELLECTUAL PROPERTY DETAILS
Patents Granted:
US10320785B2
US11165568B2
US12003620B2
KR102413497B1
CN113647051B
JP7571954B2
